SharePoint Audit Logs to Improve Corporate Security
Every company faces an increasing exposure to cyber threats, data theft, and security incidents that can compromise operations, reputation, and compliance.
SharePoint Online is the platform for managing corporate content and data that can help prevent these issues. With its auditing capabilities, in particular, it provides organizations with the necessary tools to monitor activities within the digital workplace.
Among these capabilities, the audit logs play a central role, as they allow for detailed tracking of all activities occurring within corporate systems, offering a clear view of who does what, when, and how.
In this guide, we will explore what audit logs in SharePoint are and what they are used for. We will also review some best practices and examples to better understand how to use them to protect your company.

What you will find in this article
- SharePoint Audit Logs: What are they?
- How to configure audit logs in SharePoint
- SharePoint Audit Logs: Which activities should you monitor?
- How to analyze audit log reports in SharePoint
- SharePoint Audit Logs: How do they improve security?
- Best practices for using SharePoint audit logs
- SharePoint Audit Logs: a practical use case
SharePoint Audit Logs: What are they?
Audit logs are a feature integrated into SharePoint and Microsoft 365 designed to monitor activities within a site collection, providing a detailed record of the actions performed by users and administrators.
With audit logs, it is therefore possible to track:
- document edits
- file deletions in the archive
- changes to user permissions
- etc.
They can be described as a transparent archive, where all significant interactions within the company's SharePoint environment can be retrieved. Like a 24/7 active camera, it allows you to record everything that happens in the digital workplace.
It is important to note that audit log features vary slightly depending on the version of the platform being used.
In SharePoint Server, logs can be configured directly from the site and offer a high level of customization.
In SharePoint Online, on the other hand, auditing features have been integrated with Microsoft Purview, a unified solution that centralizes the monitoring and management of activities not only for SharePoint but also for other Microsoft 365 tools.
This integration represents an important evolution, as it both improves the efficiency of log management and enables the use of advanced features such as centralized data analysis and the ability to export detailed reports.

Why monitor activities in SharePoint?
Every action tracked in the logs represents a checkpoint that can be analyzed to protect company data and improve internal governance.
Among the main advantages is the ability to identify unauthorized access.
The ability to detect suspicious activities, such as massive file deletions or unexpected changes to security settings, allows you to interpret signals that may point to cybersecurity threats.
Knowing who has viewed, modified, or shared a document can make the difference between a potential security incident and a well-protected system.
An audit log can also reveal if an unauthorized user attempted to access a restricted folder, allowing you to intervene by revoking their permissions or strengthening the security measures of the entire infrastructure.
It's like a thief trying to open our front door: what’s the first thing we would do? Change the lock.
In terms of regulatory compliance, regulations such as the GDPR (related to the protection of personal data and privacy compliance) and international standards like ISO 27001 (which defines the requirements for optimizing an information security management system) require companies to demonstrate their ability to protect the data they manage and to monitor activities related to it. This is where SharePoint security logs provide a solid foundation for generating detailed reports useful during internal or external audits.
Finally, monitoring activities supports corporate records management.
This ensures that document changes are tracked and that data is always recoverable: a particularly useful feature in contexts where it is necessary to trace the history of a file.
How to configure audit logs in SharePoint
To leverage the potential of audit logs, it is necessary to configure them properly. To do so, a few steps must be followed. In SharePoint Online, auditing features are integrated into the Microsoft Purview Compliance Center.
The recording of user and admin activities is generally enabled by default.
To check the status or to view the logs, you can access the Microsoft 365 Admin Center with admin privileges and:
- Access the Microsoft Purview Compliance Center by selecting "Show all" and then "Compliance" in the Microsoft 365 Admin Center section dedicated to administrators.
- In the left-hand menu, select "Solutions" and then "Audit." Then click "Search audit log" to access the search page.
- Define parameters such as activities, date ranges, users, files, or sites; then start the search to view the relevant results.
Although activity recording is generally active by default, there might be exceptions or specific company configurations that require checking the status of the audit log.
Additionally, it may take from 30 minutes to 24 hours for the data to become available after enabling or modifying the auditing settings.
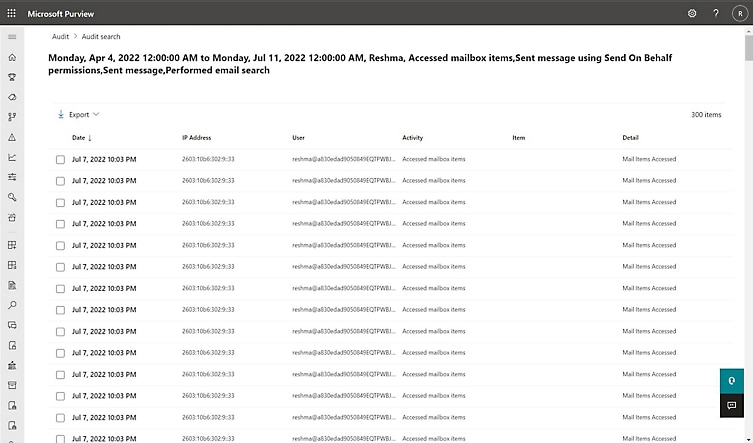
Searching for SharePoint Online audit logs in Microsoft Purview
SharePoint Audit Logs: Which activities should you monitor?
SharePoint audit logs can monitor a wide range of activities, providing a detailed overview and detecting anomalies that could hide security risks for your company's digital workplace environment.
Which events can be tracked in audit logs? Let’s mention a few.
Document edits and deletions
When a user edits or deletes a document in SharePoint, the logs record specific details, such as the user’s name, the date and time of the action, and the file involved. This is useful not only to resolve incidents, like an accidental deletion, but also to prevent recurring abuses or errors over time.
Moreover, in case of deletions, the logs provide a reference to recover files from backups.
Permission and account changes
The logs closely monitor any changes made to access permissions, including changes to a site’s, library’s, or individual file’s permissions.
In doing so, they help prevent unauthorized users from accessing confidential content. For example, if an administrator assigns editing rights to an external user, the logs record the administrator’s name, the recipient user, and the level of access granted.
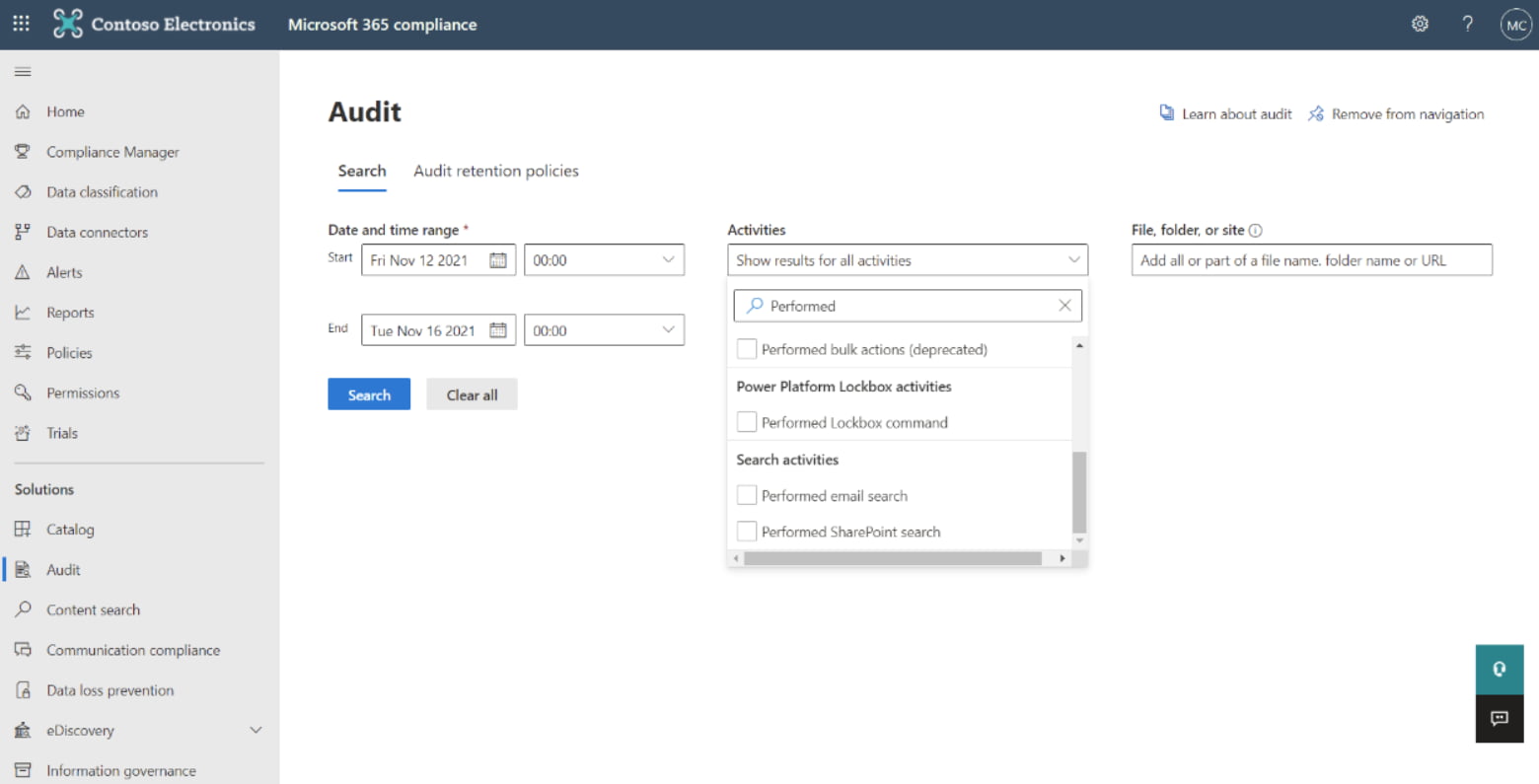
Filtering activities recorded by audit logs
Search queries
Every time a user uses the search function in SharePoint, the logs record the searched terms and the results displayed. This type of tracking helps identify suspicious behavior patterns.
In fact, if a user performs many searches using sensitive keywords (such as "salaries," "confidential contracts"), it could be a sign of an attempt to access unauthorized confidential information.
Beyond security, monitoring search queries also offers organizational benefits, as the data can be analyzed to optimize content architecture, making it easier for users to find what they need.
Workflows and other system activities
Automated workflows, also known as workflows, are processes that perform specific actions in SharePoint, such as approving new documents or sending notifications. Audit logs track these activities, providing details about who triggered the workflow, when it was executed, and what outcomes it produced.
Let’s take an approval workflow for a contract: the logs can show whether a document was approved by all required parties or if the process was interrupted due to an error.
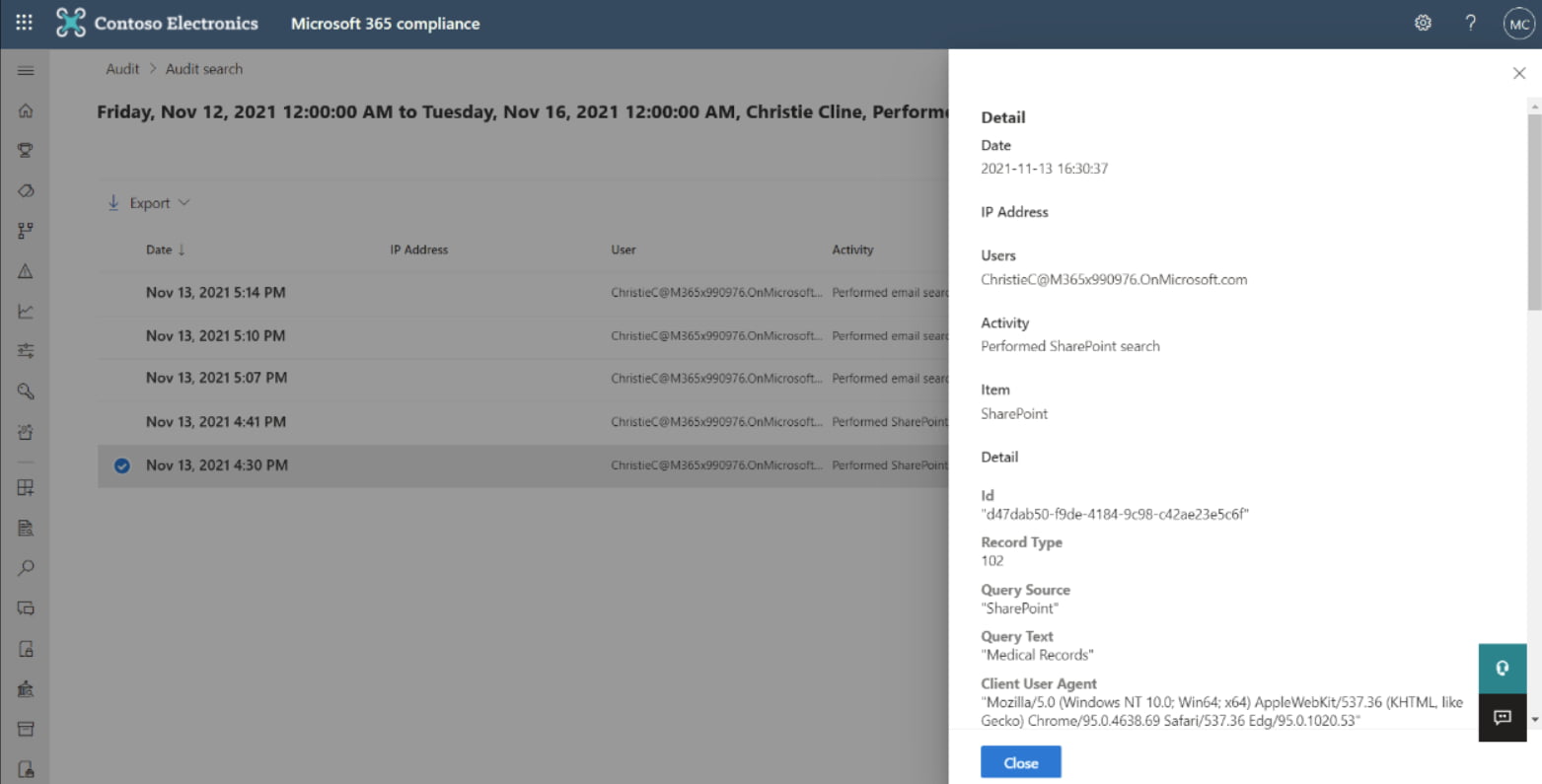
Analyzing the activities recorded by audit logs
How to analyze audit log reports in SharePoint
Audit log reports can be viewed directly in the Compliance Center via Microsoft Purview Audit or exported for more in-depth analysis.
You can filter the data based on specific criteria, such as date range, user, or activity type.
An IT manager can analyze a colleague’s access activities during a specific period to check for any suspicious behavior, while a project manager can review changes made to key documents during project development.
Exporting reports to Excel format allows for deeper analysis using filters and creating charts and pivot tables. Excel’s features can be useful for identifying recurring trends, such as frequent access to certain files outside of working hours.
SharePoint, for its part, generates a series of standard reports for common events. These include:
- Content changes: provides details about which files were modified, when, and by whom.
- Deletion and restoration: tracks the deletion of files or folders, along with any restorations.
It’s important to remember that access to these reports and the level of data detail depend on the Microsoft 365 license in use. For advanced features or extended data retention periods, a Microsoft 365 E5 license or a Microsoft Purview add-on may be required.
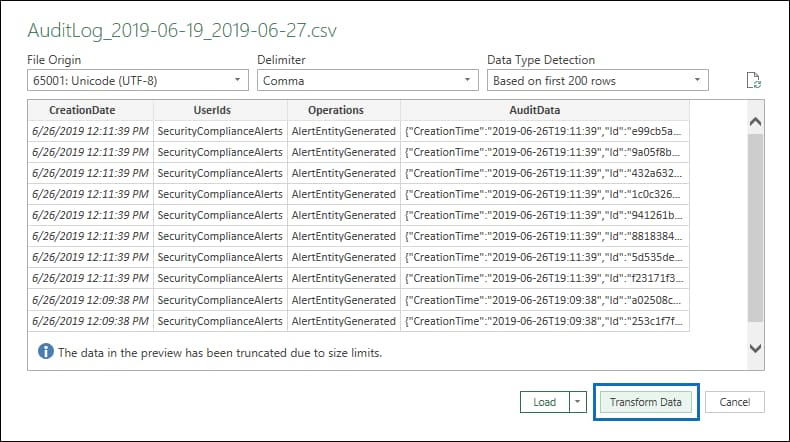
Importing and analyzing SharePoint audit logs in Excel
Finally, through PowerShell, it is possible to create custom reports.
This way, it becomes possible to filter specific events or combine data from multiple site collections. For example, a company could use PowerShell integration to monitor only activities related to a project and external user access to sensitive documents.
A PowerShell script can also automate the creation of a weekly report that includes only events related to permission changes on a site collection, providing a snapshot of the most important activities that have occurred.
SharePoint Audit Logs: How do they improve security?
Audit logs are not just a passive tool used solely to record events, but can be used proactively to enhance corporate security.
Let’s take a practical example to better understand this.
If a user accesses a site collection outside regular working hours, it could signal a potential attack or a compromised account. By analyzing the logs, it becomes possible to take preventive measures such as temporarily disabling an account or enabling additional verifications.
Sharing documents with external users is a common practice in many companies, but it carries significant risks if not properly monitored.
In this case, audit logs allow you to track which files were shared, with whom, and when. An organization could thus discover that a confidential document was mistakenly shared with an unauthorized user and intervene immediately to revoke access.
In more complex scenarios, such as collaborating with external users, logs can be used to ensure that company policies are respected, preventing data leaks or misuse.
In this regard, we can mention the integration with Microsoft Sentinel, a cloud-based security information and event management platform that allows correlating activity logs from different sources to identify and mitigate major threats.
With Sentinel, administrators can centralize log data, analyze it using artificial intelligence, and create automation rules to respond to incidents in real time.
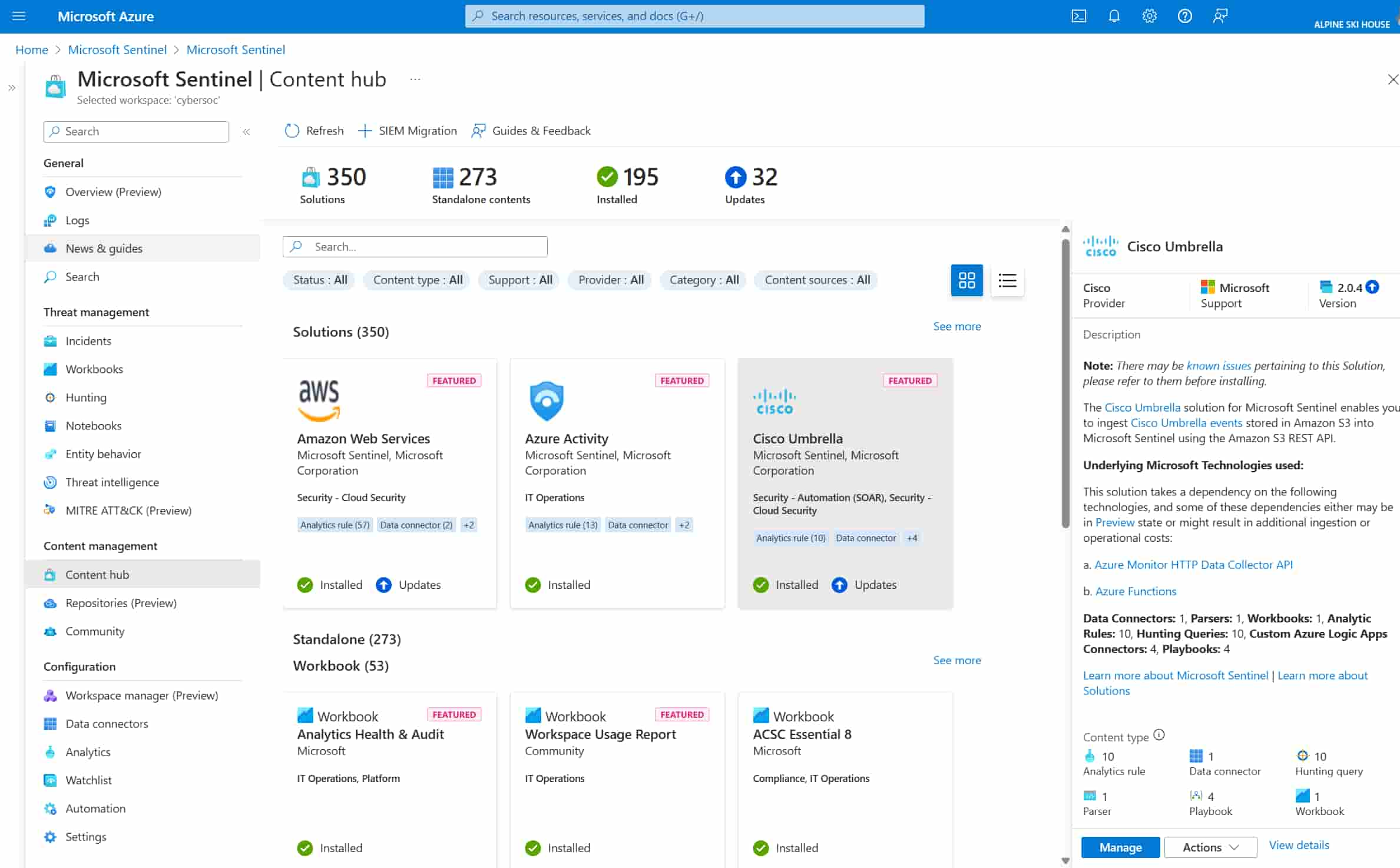
Overview of Microsoft Sentinel
Best practices for using SharePoint audit logs
Proper use of audit logs goes beyond technical configuration and requires a strategic and proactive approach involving the entire organization.
There are some best practices that can be adopted: let’s take a look at them together.
Establish a clear auditing policy
An auditing policy is the starting point and should include the following elements:
- Types of events to monitor: Clearly define which activities should be tracked, such as document changes, unauthorized access, and data sharing.
- Data retention: Establish how long logs should be kept, considering applicable regulations (e.g., retention for specific periods).
- Roles and responsibilities: Identify who within the organization is responsible for analyzing the logs and responding to events.
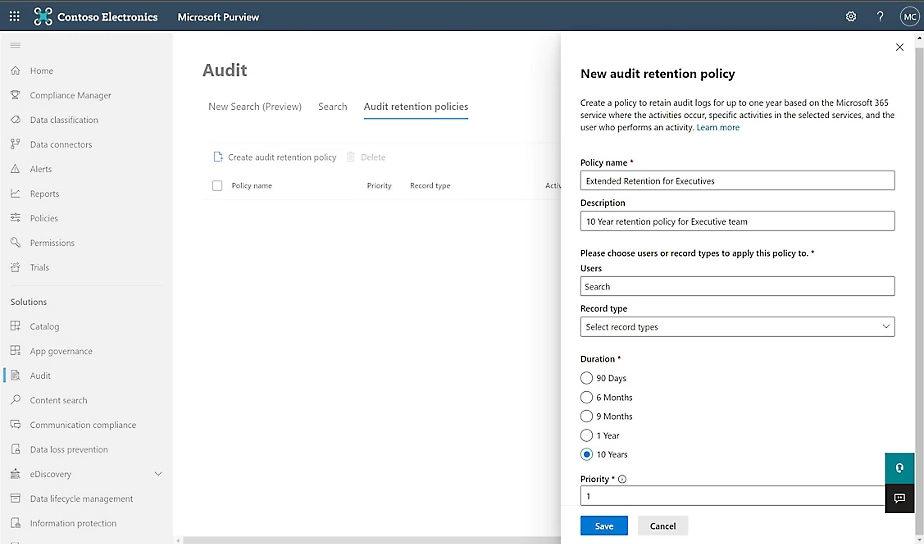
Creating new data retention policies for SharePoint audit logs
Involve IT and Compliance teams
Monitoring audit logs should not be the exclusive responsibility of the IT team but should also involve compliance teams. A shared monthly report could be created to highlight critical activities such as permission changes or access to sensitive data, ensuring both teams are constantly aligned on potential issues and the adopted resolution methods.
Train users
If your team is properly trained on the main security aspects and the available tools to manage it, both personally and organizationally, half the work is already done.
All users should be aware of how to use audit logs within the company's digital workplace. Proper training sessions are often the simplest and most effective way to educate colleagues about the risks associated with non-compliant behaviors and to show how logs are a tool to protect both the company and its workers.
Integrate other Microsoft 365 tools
Many companies decide to adopt third-party solutions to manage more complex security management scenarios. In fact, standard features offered by SharePoint are not always considered sufficient to properly analyze and, above all, respond to threats.
However, our recommendation is to fully leverage your company's Microsoft licenses to maximize the possibilities for analysis, monitoring, and governance without wasting investments on standalone solutions that are poorly integrated into the Microsoft 365 ecosystem.
Share data with Power BI for advanced visualizations
Power BI is a tool capable of transforming complex data into intuitive visualizations.
Data collected from SharePoint logs can be loaded into Power BI to create dynamic reports and custom dashboards, offering deeper insights compared to Excel tables.
As a practical example, an IT manager can create a dashboard that shows real-time activities related to access to sensitive documents, highlighting anomalies such as access attempts during unusual hours. Log data can also be used to generate usage trends, identifying which areas of the platform are most frequently visited by users.
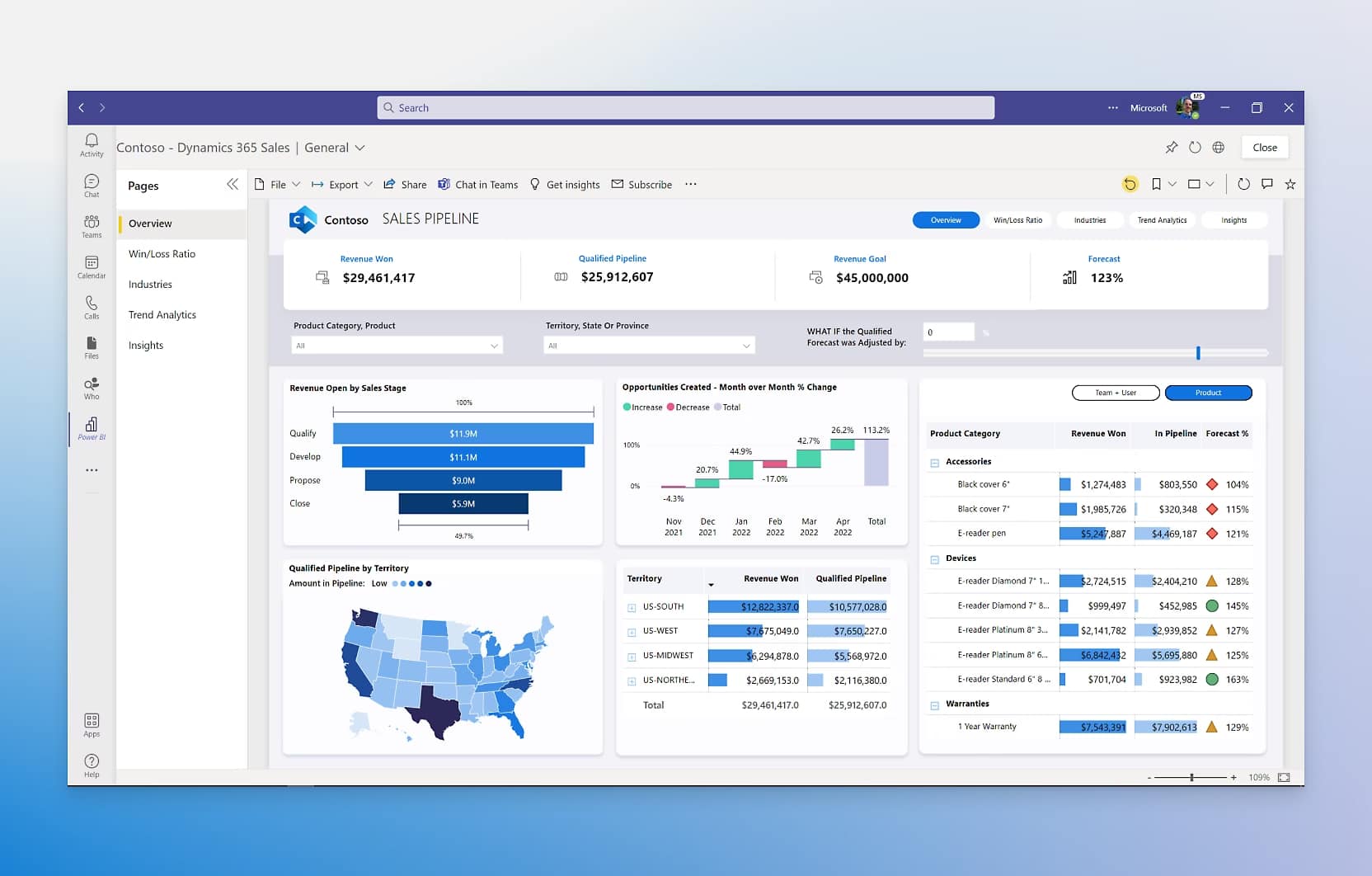
Overview of the available visualizations in Power BI
Use logs to improve Teams and OneDrive governance
Governance of Microsoft Teams and OneDrive is closely linked to SharePoint, as most files and activities are managed through this platform.
In this case, audit logs can be used to:
- Monitor sharing activities within Teams, identifying any unauthorized actions or security risks.
- Analyze OneDrive usage to ensure data management complies with company policies.
Microsoft services monitored through audit logs
Integrate Microsoft Defender for Office 365
Microsoft Defender for Office 365 provides advanced protection against threats such as phishing and malware. By integrating SharePoint log data with this tool, you can:
- Correlate events recorded in the logs with potential threats identified by Defender;
- Receive automatic alerts when suspicious activities in SharePoint are associated with abnormal behaviors flagged by Defender.
If Microsoft Defender detects a phishing attempt involving a file in SharePoint, audit logs can help determine who accessed the file and what actions were taken, facilitating a rapid and targeted response.
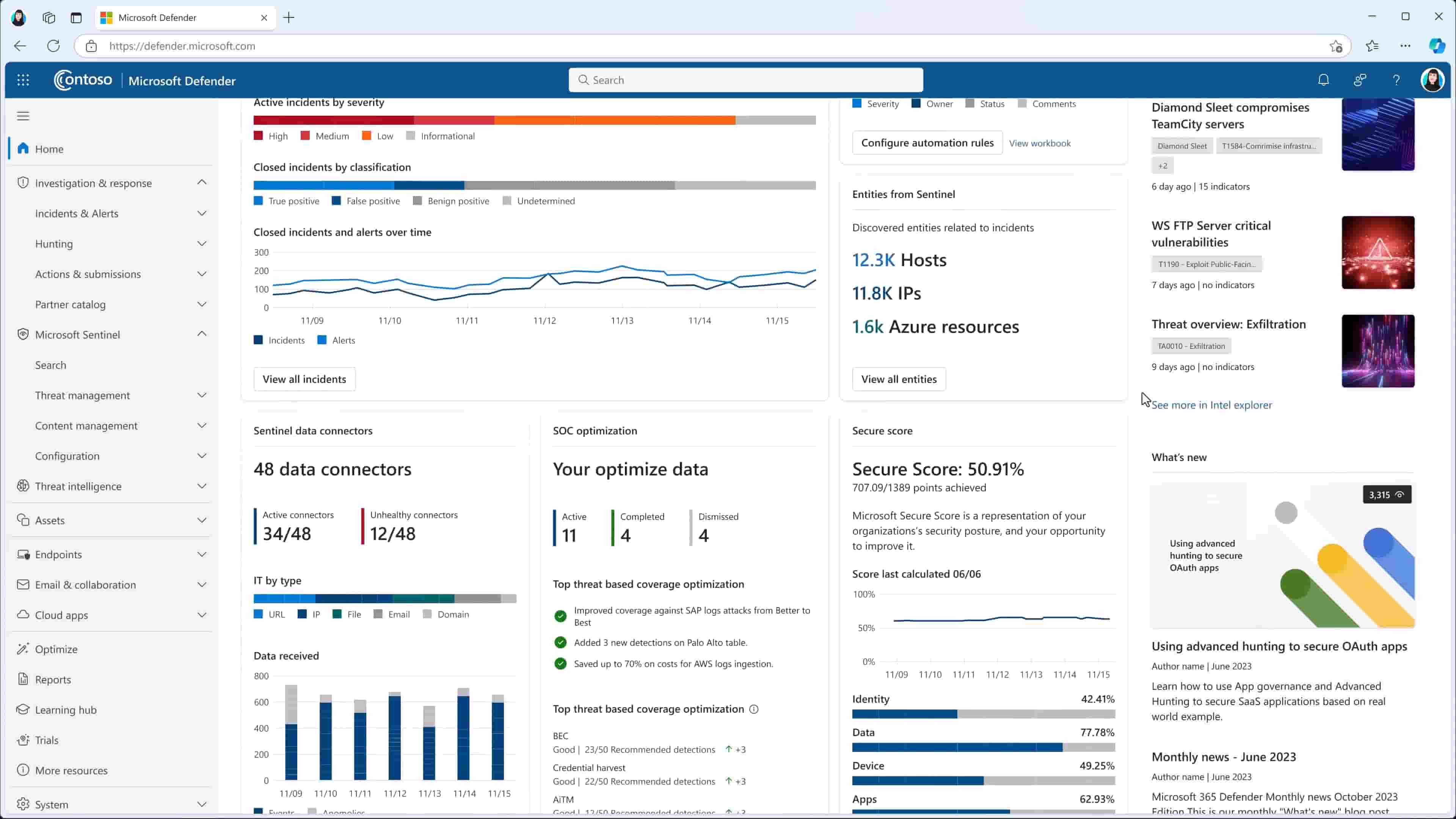
Overview of Defender for Office 365
SharePoint Audit Logs: a practical use case
After so much theory, we decided to conclude this guide by explaining how to improve corporate security through SharePoint audit logs with a small practical example taken from our experience with a client.
Let's start by simulating a company with about 500 employees, where SharePoint Online is used as the main platform for document management.
The IT managers decide to configure the audit logs to monitor:
- Access to confidential documents
- Permission changes on site collections
- Sharing activities with external users
After enabling the logs through the Compliance Center in Microsoft Purview, the company implements a Power BI dashboard that collects and displays key activities, highlighting anomalous events such as off-hours access or unauthorized changes.
After a six-month monitoring activity, the company records the following results:
- Thanks to the audit logs, every activity on documents is tracked, facilitating internal audits and ensuring compliance.
- The logs help identify an attempted unauthorized access to the finance department's data, allowing rapid intervention and blocking of the involved user.
- The centralized view of activities reduces the time needed to analyze data and respond to incidents.
Thus, with a couple of tools and a minimal investment of resources, any company can strengthen its security posture. However, if internal technical skills are lacking to make the most of the available Microsoft technology, it is always possible to seek the support of consultants, including the experts from our team, certified Microsoft Gold Partner with decades of experience in the implementation, management, and customization of digital workplaces based on Microsoft 365.
Need a hand managing your SharePoint sites?
We've got more than 100 on deck to support your company in:
- Distributing the right permissions to users
- Ensuring the security of shared information
- Improving document and resource management
- Developing custom web parts and branded graphics
Giuseppe Marchi
Microsoft MVP for SharePoint and Microsoft 365 since 2010.
Giuseppe is the founder of intranet.ai and one of the top experts in Italy for all things Microsoft 365. For years, he has been helping companies build their digital workspace on Microsoft's cloud, curating the people experience.
He organizes monthly online events to update customers on what's new in Microsoft 365 and help them get the most out of their digital workplace.

FAQ about SharePoint audit logs
What is an audit log in SharePoint?
An audit log, or control log, is a record that allows you to monitor all activities performed within a SharePoint site collection. It is used to track changes, accesses, shares, and changes in user permissions, offering a detailed and transparent view of interactions in the digital workplace.
How are audit logs configured in SharePoint Online?
In SharePoint Online, activity logging is integrated into the Microsoft Purview Compliance Center. Access to the logs is available through the Microsoft 365 Admin Center, in the dedicated Audit section, where you can perform searches by setting parameters such as dates, users, or specific files.
What types of activities are monitored?
Audit logs can track document edits and deletions, changes to permissions and accounts, user-performed searches, and the execution of automated workflows. Each event is recorded with useful details for analysis and risk prevention.
How are audit log data analyzed?
Data can be analyzed directly within the Compliance Center or exported to Excel for further processing, such as filters and charts. It is also possible to use PowerShell to create custom reports or Power BI for more advanced interactive visualizations.
What is the value of audit logs for corporate security?
Audit logs help identify anomalous activities, suspicious accesses, or unauthorized sharing. These elements are essential for preventing breaches, responding promptly to incidents, and ensuring compliance with regulations such as GDPR or ISO 27001.
With which Microsoft tools are audit logs integrated?
SharePoint logs can be integrated with Microsoft Sentinel for event correlation, with Microsoft Defender for Office 365 for protection against phishing and malware, and with Power BI to create advanced dashboards. They also work with Teams and OneDrive, which share the same document infrastructure.
How long are logs retained?
The retention period varies depending on the Microsoft 365 license in use. Standard features are available in basic licenses, while advanced features and extended retention periods require an E5 license or specific add-ons for Microsoft Purview.
Is it possible to improve the governance of Teams and OneDrive through audit logs?
Yes. Logs can be used to monitor file sharing in Teams and verify the proper use of OneDrive, helping to ensure that data management aligns with corporate policies.
Is a policy necessary for using audit logs?
An auditing policy is highly recommended. It should define the activities to be monitored, the data retention periods, and internal responsibilities. Only in this way can logs be effectively managed to ensure security and transparency.
Who should manage and analyze the logs?
The responsibility is not solely on the IT team. It is essential to also involve the compliance team to ensure shared analysis and coordinated response to critical events. Producing regular reports helps maintain high awareness of potential anomalies.
Keep on reading
Why Choose SharePoint for Your Intranet?



Let’s explore why SharePoint is the best choice for your intranet, comparing it with solutions like WordPress, Intranet Connections, Drupal, and others.
SharePoint Admin Center: How to Manage SharePoint Sites



The Admin Center is the web interface for managing sites, content, and data security in SharePoint. Here's how to make the best use of its features.
Artificial Intelligence: What It Is and Examples in the Intranet



What does “artificial intelligence” really mean? Let’s explore the concept of AI and the possible applications within the SharePoint Online intranet.


